:)-separated list of OpenSSL ciphers (list aka cipher-spec string)
| prefix | usage |
|---|---|
| (none) | add cipher to list |
| + | move cipher to the current location in list |
| - | remove cipher from list (can be added later again) |
| ! | kill cipher from list completely (can not be added later again) |
SSLCipherSuite [protocol] cipher-spec
SSLProtocol all -SSLv2 -SSLv3 -TLSv1
-SSLv2 +SSLv3 -SSLv3 +TLSv1 -TLSv1 +TLSv1.1 +TLSv1.2This makes things uselessly complex IMHO .
SSLProtocol all -SSLv2 -SSLv3 -TLVv1This line actually enables an obsolete protocol . Exercise : find what's wrong. The more protocols to ban, the more likely this error is.
SSLProtocol -all +TLSv1.2
SSLProtocol: Illegal protocol 'TLSv1.3'means it is not supported by your current version.
ServerAlias *.example.com matches foo.example.com but also foo.bar.example.com and foo.bar.baz.example.com.
When a request arrives, the server will find the best (most specific) matching VirtualHost argument based on the IP address and port used by the request. If there is more than one virtual host containing this best-match address and port combination, Apache will further compare the ServerName and ServerAlias directives to the server name present in the request.
If you omit the ServerName directive from any name-based virtual host, the server will default to a FQDN derived from the system hostname. This implicitly set server name can lead to counter-intuitive virtual host matching and is discouraged.
If no matching ServerName or ServerAlias is found in the set of virtual hosts containing the most specific matching IP address and port combination, then the first listed virtual host that matches that will be used.
RewriteEngine on, then reload the configuration.For further debugging, consider mod_rewrite's logging directives.
"-" if not available. This information is highly unreliable and should almost never be used except on tightly controlled internal networks"-" if the document is not password-protected"-"When the Apache HTTP Server manages its child processes, it needs a way to wake up processes that are listening for new connections. To do this, it sends a simple HTTP request back to itself. This request will appear in the access_log file with the remote address set to the loop-back interface (typically 127.0.0.1 or ::1 if IPv6 is configured). If you log the User-Agent string (as in the combined log format), you will see the server signature followed by (internal dummy connection) on non-SSL servers. During certain periods you may see up to one such request for each httpd child process.
In 2.2.6 and earlier, in certain configurations, these requests may hit a heavy-weight dynamic web page and cause unnecessary load on the server. You can avoid this by using mod_rewrite to respond with a redirect when accessed with that specific User-Agent or IP address.
(source)
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteCond %{HTTP_USER_AGENT} ^.*internal\ dummy\ connection.*$ [NC]
RewriteRule .* – [F,L]
</IfModule>
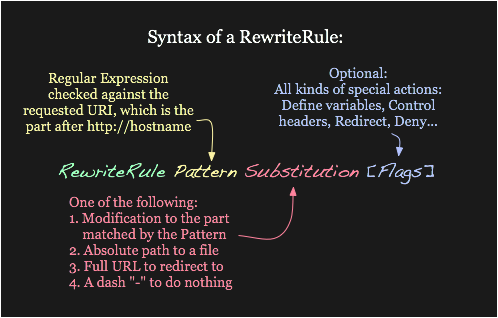
Syntax : RewriteRule Pattern Substitution [Flags]
| Given Rule | Resulting Substitution |
|---|---|
| ^/somepath(.*) /otherpath$1 | /otherpath/pathinfo |
| ^/somepath(.*) /otherpath$1 [R] | http://thishost/otherpath/pathinfo via external redirection |
| ^/somepath(.*) http://thishost/otherpath$1 | /otherpath/pathinfo |
| ^/somepath(.*) http://thishost/otherpath$1 [R] | http://thishost/otherpath/pathinfo via external redirection |
| ^/somepath(.*) http://otherhost/otherpath$1 | http://otherhost/otherpath/pathinfo via external redirection |
| ^/somepath(.*) http://otherhost/otherpath$1 [R] | http://otherhost/otherpath/pathinfo via external redirection (the [R] flag is redundant) |
To make redirects without keeping the query string : http://foo?123 ==> http://bar just do : ^.* http://bar/? http://stackoverflow.com/questions/9374566/htaccess-remove-query-string-from-url-no-redirection http://httpd.apache.org/docs/current/en/mod/mod_rewrite.html (See "Modifying the Query String" paragraph)
In .htaccess context, with /physical/path/to/somepath/.htaccess having RewriteBase /somepath and a request such as : GET /somepath/localpath/pathinfo
| Given Rule | Resulting Substitution |
|---|---|
| ^localpath(.*) otherpath$1 | /somepath/otherpath/pathinfo |
| ^localpath(.*) otherpath$1 [R] | http://thishost/somepath/otherpath/pathinfo via external redirection |
| ^localpath(.*) /otherpath$1 | /otherpath/pathinfo |
| ^localpath(.*) /otherpath$1 [R] | http://thishost/otherpath/pathinfo via external redirection |
| ^localpath(.*) http://thishost/otherpath$1 | /otherpath/pathinfo |
| ^localpath(.*) http://thishost/otherpath$1 [R] | http://thishost/otherpath/pathinfo via external redirection |
| ^localpath(.*) http://otherhost/otherpath$1 | http://otherhost/otherpath/pathinfo via external redirection |
| ^localpath(.*) http://otherhost/otherpath$1 [R] | http://otherhost/otherpath/pathinfo via external redirection (the [R] flag is redundant) |
| ^localpath(.*) http://otherhost/otherpath$1 [P] | http://otherhost/otherpath/pathinfo via internal proxy |
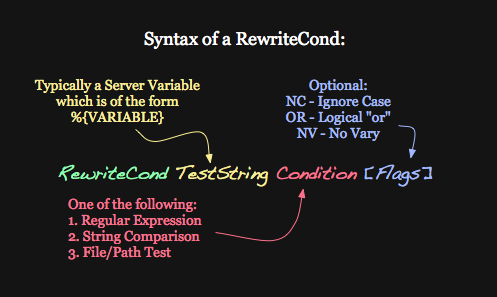
In the RewriteCond TestString Condition [Flags] statement, Condition is usually a Perl-compatible regex. This answers all questions about wildcards
When more than one RewriteCond is specified, they must all match for the RewriteRule to be applied.
This outputs /srv/ssl/ca.cert.pem, which is the CA's certificate. This can already be shared publicly provided Apache can handle its MIME type :
<VirtualHost *:443> ServerName ssl.acme.com DocumentRoot /var/www/ssl.acme.com SSLEngine On SSLProtocol +TLSv1 +TLSv1.1 +TLSv1.2 -SSLv2 -SSLv3 # Disable obsolete SSL versions SSLCertificateFile /srv/ssl/acme/acme.cert.pem SSLCertificateKeyFile /srv/ssl/acme/acme.key.nopass.pem </VirtualHost>
<IfModule mod_ssl.c> Listen 443 NameVirtualHost *:443 </IfModule>
NameVirtualHost is deprecated since Apache 2.3.11 (sources : 1, 2). This solution may not work as expected or generate errors.
This fixes the [warn] _default_ VirtualHost overlap on port 443, the first has precedence error (source).Running multiple web sites that allow HTTPS connections on the same Apache httpd server is problematic. Typically, HTTP virtual servers (the individual web sites) use named virtual hosting, where the virtual host which serves the site is chosen based on the host name specified in the HTTP Host header.
Named virtual hosting does not work for HTTPS because the server cannot interpret the Host header until the connection has been made, and making the connection requires the completion of the SSL encryption handshake used by HTTPS.
SSL certificates (without extensions) can only have a single server host name as their subject, and thus the certificate and connection will only work for a single host name. As a result, the named virtual hosting mechanism never has a chance to operate on the incoming connection and the only remaining way to host multiple sites is to add multiple IP addresses to the host and use IP-based virtual servers.
This allows a certificate to list a number of host names for which it is valid. For example, a single certificate with www.example.com as its (single) subject could list www.example.com, www.example.org, and webapp.example.com as alternate names. The certificate would be recognized as valid for any of those host names.
More details in RFC 3280.Configuration directives discussed here are deprecated for Apache 2.4.x. Read this article for solution and links.
Order Deny,Allow Deny from all Allow from apache.org
Order Allow,Deny Allow from apache.org Deny from foo.apache.org
Order Allow,Deny or Order Deny,Allow works on 3 steps :
Allow,Deny or Deny,Allow matters because the last matching rule applies.Allow from ... and Deny from ... lines in the configuration file doesn't matter.Order Deny,Allow
Deny from all
Allow from apache.org
Deny from allAllow from apache.orgDeny from allOrder Allow,Deny Allow from apache.org Deny from foo.apache.org
Allow from apache.orgAllow from apache.orgDeny from foo.apache.orgOrder Allow,Deny
Allow from all
Deny from apache.org
Allow from allDeny from apache.orgAllow from all # Get images from PROD if not available here.
RewriteCond %{DOCUMENT_ROOT}/$1 !-f
RewriteRule ^/(var/[^/]+/storage/.*)$ http://www.example.com/$1 [R,L,NS]
Some file formats are already compressed, meaning that any extra compression won't have any noticeable effect on filesize, but will increase processing time.
<FilesMatch "\.ph(p3?|tml)$">, declaring which files are considered as .php files.<FilesMatch "\.ph(p3?|p5|tml)$">Other solution with a2enmod php5 (not tested)
<Directory /var/www/myCgiApp> Options Indexes FollowSymLinks MultiViews +ExecCGI AllowOverride None Order allow,deny allow from all </Directory>
Don't forget to have a look at the error log : tail -f /var/log/apache2/error.log