X11Forwarding noForwardX11Trusted no
ClientAliveInterval n ClientAliveCountMax 0
MaxAuthTries 2 LoginGraceTime 30
KexAlgorithms curve25519-sha256, curve25519-sha256@libssh.org, diffie-hellman-group16-sha512, diffie-hellman-group18-sha512, diffie-hellman-group-exchange-sha256 Ciphers chacha20-poly1305@openssh.com, aes256-gcm@openssh.com, aes128-gcm@openssh.com, aes256-ctr, aes192-ctr, aes128-ctr MACs hmac-sha2-256-etm@openssh.com, hmac-sha2-512-etm@openssh.com, umac-128-etm@openssh.com HostKeyAlgorithms ssh-ed25519, ssh-ed25519-cert-v01@openssh.com, sk-ssh-ed25519@openssh.com, sk-ssh-ed25519-cert-v01@openssh.com, rsa-sha2-256, rsa-sha2-512, rsa-sha2-256-cert-v01@openssh.com, rsa-sha2-512-cert-v01@openssh.com
Port 443 ListenAddress 192.168.1.5Or :
ListenAddress 192.168.1.5:443
Compression no
#!/bin/bash interface=eth1 sshPort=22 iptables -I INPUT -p tcp --dport $sshPort -i $interface -m state --state NEW -m recent --set iptables -I INPUT -p tcp --dport $sshPort -i $interface -m state --state NEW -m recent --update --seconds 60 --hitcount 5 -j DROPOr consider fail2ban to block brute force attacks (if you don't mind it eating your CPU...).
sshd : 192.168.1.2 172.16.23.12
| Key type | Length [bits] | Comment | ||
|---|---|---|---|---|
| min. | default | max. | ||
| DSA | exactly 1024 | Deprecated since OpenSSH 7.0, should not be used anymore (source, details) | ||
| ECDSA | ssh-keygen -b determines the key length by selecting from one of three elliptic curve sizes: 256, 384 or 521 bits. All other values will fail. |
|
||
| Ed25519 | keys have a fixed length and ssh-keygen -b flag will be ignored |
|
||
| RSA | 1024 | 2048 |
|
|
# and empty lines are considered as comments and ignoredmarkers : one of @cert-authority or @revokedhostnames :
? or *, negation !, or stuff like : [hostname]:nonStandardPortNumber| : 1 hashed host name only, no wildcardskeyType : taken directly from the host public keybase64-encoded key : taken directly from the host public keycomment : for humans only, field ignored| characterexample.com,12.34.56.78 ssh-rsa AAAAB3NzaC1yc2EAAAABIEYsdlLJizHhbn2mUjvSAHQqZETYP8 [87.65.43.21]:443 ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJ/ycvU99wR2V5R0DoRFUKLJu5gHHzbTeclrKCNazPF6 [myServer]:443 ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJ/ycvU99wR2V5R0DoRFUKLJu5gHHzbTeclrKCNazPF6 otherServer,10.200.2.133 ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIFJedssLBKbi/JNVr+D/LjBPQxz/lh0QWp/9Gqq1lQE4 <----------------------- hostname -------------------------> <---- keyType ----> <------------------------ host public key -------------------------------> <- comment -> |1|grfd/OaC6DWyOMR7SnNf9B/16VA=|2uogKOBT5cudir2KPB7osUhcGw0= ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItboumF44X/ijdaL6wPg9EGXbDKS9Euljb1QzNZ+URKQDHNQfvDZI= foo bar baz |1|dsRkLZMgihkLV7iIYaOj+c2E9tQ=|jv1y+ZlW6V5Ur2+ZokGAZqx01Ks= ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbLCnAw+yUtX4Kk200cPqrHaujTP0k9HfMD0ePH35GNI6cw8Kbs4= hello world |1|19DOvudcdXmK3NyfRa3bKdWDF4k=|NpVnuE2D07Je9aa5i/TUXz5ZAnE= ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbLCnAw+yUtX4Kk200cPqrHaujTP0k9HfMD0ePH35GNI6cw8Kbs4= ga bu zo meu
ssh_exchange_identification: Connection closed by remote host
| Flag | Usage |
|---|---|
| -s | forces generation of Bourne shell (/bin/sh) commands on stdout. By default the shell is automatically detected. |
bob 982 0.0 0.0 11088 328 ? Ss Oct08 0:00 /usr/bin/ssh-agent startxfce4
$SSH_AGENT_SOCK$SSH_AGENT_SOCK testifies that ssh-agent is runningenv | grep SSH_
SSH_AUTH_SOCK=/run/user/1000/keyring/ssh
2048 SHA256:cMdVUp8pTJGbLYS6Ngrl5odnFYGhoBXGY1p8pTJGbLTk+drlkgE /home/kevin/.ssh/myPrivateKey (RSA)
ssh-add myKey in ~/.bashrc. Instead, use AddKeysToAgent.| Flag | Default | Usage |
|---|---|---|
| BindInterface | Use the address of the specified interface on the local machine as the source address of the connection
This feature was introduced by OpenSSH 7.7. As of June 2019, it must be installed —on Debian Stretch— via the testing repository (details, sources : 1, 2). |
|
| Compression | no | Specifies whether to use compression |
| ControlMaster | Share multiple sessions over a single network connection. Values :
|
|
| ControlPath | Specify
|
|
| ControlPersist | Used with ControlMaster to specify how the master connection should remain open in the background :
|
|
| HashKnownHosts | no | hash host names and addresses when they are added to ~/.ssh/known_hosts so that they do not visually reveal identifying information if the file's contents are disclosed. |
| Include someFile |
|
|
| LogLevel LEVEL | (explicit) | |
| ProxyCommand | Specifies the command to use to connect to the server, typically when there is an intermediate hop between the SSH client and server (examples : 1, 2, 3)
|
|
| ProxyJump | Specify one or more jump proxies :
|
|
| ServerAliveInterval n | send keepalivemessages every n seconds when the connection is idle (details). Defaults to 0 (i.e. disabled). |
|
| StrictHostKeyChecking | ask |
If you're using temporary VMs and want to avoid polluting ~/.ssh/known_hosts with irrelevant host keys, see UserKnownHostsFile instead.
|
| UserKnownHostsFile someFile | ~/.ssh/known_hosts | specify one or more (space-separated) files to use for the user host key database
To connect to an host without registering its host key into ~/.ssh/known_hosts (useful with VMs having a short lifespan) :
|
ProxyCommand :
Host sshHost ProxyCommand ssh sshProxy nc %h %p 2> /dev/null
ProxyCommand with the -W flag :
Host sshHost ProxyCommand ssh sshProxy -W %h:%p
ProxyJump :
Host sshHost ProxyJump sshProxy
Host HAL this can be an alias, an IP address, a negated expression or a pattern (trick about patterns lists) HostName realHostname if you specified an alias above Port 443 Port to connect to on the remote host. Defaults to 22 User DrEinsteinVonBrainstorm IdentityFile ~/.ssh/myPrivateKey ProxyCommand ssh -e none hop exec nc -w 5 %h %p Go through hop host. If hop is an HTTP proxy, read this. AddKeysToAgent yes details ForwardAgent yes
,), but when they apply to the Host directive, they are whitespace-separated.Host * this is a valid statement (details : 1, 2) ServerAliveInterval 120 Keep SSH sessions alive LogLevel QUIET hide the connection banner
sshd supports SSH1 and SSH2 protocols, but SSH1 is not secure, so it mustn't be used !
Existing connections can survive sshd restart (source) :
| File | Purpose |
|---|---|
| /etc/ssh/sshd_config | This is the main configuration file (Configuration directives). sshd can't start if this file is unavailable. |
| /etc/motd | welcome message to be displayed after a successful login, either "normal" login or via SSH (or grep Banner /etc/ssh/sshd_config ) |
| ~/.ssh/authorized_keys | list of public keys. This can also hold some configuration directives. |
| /etc/nologin | If this file exists, sshd refuses to let anyone except log in. |
| /etc/hosts.allow /etc/hosts.deny |
ACL that should be enforced by tcp-wrappers are defined here. |
| Directive | Default value | Usage |
|---|---|---|
| AcceptEnv myEnvironmentVariable | Declare environment variables that can be set by the SSH client (aka whitelist . A single AcceptEnv directive can declare several variables, separated by a space character. | |
| AllowGroups | all | SPACE-separated list of group names / pattern. Only the matching ones are allowed to log in. |
| AllowTcpForwarding | yes | Specifies whether TCP forwarding is permitted.
Disabling TCP forwarding does not improve security unless users are also denied shell access, as they can always install their own forwarders.
When SSH forwarding is still needed, it is possible to enable it to specified users only (source) :
AllowTcpForwarding no
Match User stuart
AllowTcpForwarding yes
|
| AllowUsers | all | SPACE-separated list of user names or user / user@host patterns. Only the matching ones are allowed to log in. |
| AuthenticationMethods | Any | comma-separated list of authentication methods that must be successfully completed for a user to be granted access |
| Banner | points to a banner file that can be found anywhere. The content of this banner is displayed during an SSH login, between the login name and password input. | |
| yes | whether challenge-response authentication —the keyboard-interactive authentication scheme defined in RFC-4256— is enabled. This keyboard-interactive authentication scheme could, in theory, ask a user any number of multi-faceted questions. In practice it often asks only for the user's password.
This directive has been deprecated by KbdInteractiveAuthentication
|
|
| ClientAliveCountMax n | Allow at most n unanswered requests sent by ClientAliveInterval before disconnecting the client.
The ClientAliveInterval timer is reset after sending every request.
|
|
| ClientAliveInterval n | Start a timer for n seconds before requesting client response over the encrypted channel (this has nothing to do with KeepAlive, which is a TCP setting). 0 disables this function. |
|
| Compression value | yes | Specifies whether compression is enabled after the user has authenticated successfully. value must be :
|
| DenyGroups | empty |
|
| DenyUsers | empty |
|
| GatewayPorts | no | Specifies whether remote hosts are allowed to connect to ports forwarded for the client (details) |
| HostbasedAuthentication | no | Specifies whether rhosts or /etc/hosts.equiv authentication together with successful public key client host authentication is allowed |
| IgnoreRhosts | yes | whether to ignore per-user .rhosts and .shosts files (SSH can emulate the obsolete rsh with these) during HostbasedAuthentication. The system-wide /etc/hosts.equiv and /etc/shosts.equiv are still used regardless of this setting. |
| KbdInteractiveAuthentication | yes | whether to allow keyboard-interactive authentication
ChallengeResponseAuthentication is a deprecated alias for this
|
| ListenAddress | Specifies the local addresses sshd should listen on | |
| LoginGraceTime duration | 120 seconds |
|
| Match | Introduces a conditional block. If all of the criteria on the Match line are satisfied :
|
|
| MaxAuthTries | 6 | Specifies the maximum number of authentication attempts permitted per connection. Once the number of failures reaches half this value, additional failures are logged. |
| MaxSessions | 10 |
|
| MaxStartups | 10:30:100 |
|
| PasswordAuthentication | yes | Whether password authentication is allowed |
| PerSourceMaxStartups n | none |
|
| PermitEmptyPasswords | no | When PasswordAuthentication is allowed, it specifies whether the server allows login to accounts with empty password strings. |
| PermitRootLogin value | prohibit-password |
|
| PubkeyAuthentication | yes | Whether public key authentication is allowed |
| StrictModes | yes | Specifies whether sshd should check file modes and ownership of the user's files and home directory before accepting login. This is normally desirable because novices sometimes accidentally leave their directory or files world-writable. |
| Subsystem | empty | Configures an external subsystem (e.g. file transfer daemon) |
| UseDNS | Specifies whether sshd should look up the remote host name and check that the resolved host name for the remote IP address maps back to the very same IP address. Set this to no to disable server lookups. | |
| UsePAM | no | Enables the PAM interface. Details : |
| UsePrivilegeSeparation | This option is deprecated since OpenSSH 7.5 (source) | |
| X11DisplayOffset n | Specifies the first display number available for sshd's X11 forwarding. This prevents sshd from interfering with real X11 servers. Defaults to 10. | |
| X11Forwarding | no | whether X11 forwarding is permitted
disabling X11 forwarding does not prevent users from forwarding X11 traffic, as users can always install their own forwarders
|
| Local tunnel | Remote tunnel | |
|---|---|---|
| where is the resource server located ? | away from :
|
on :
|
| where is the resource client located ? | on :
|
away from :
|
| traffic direction |
|
|
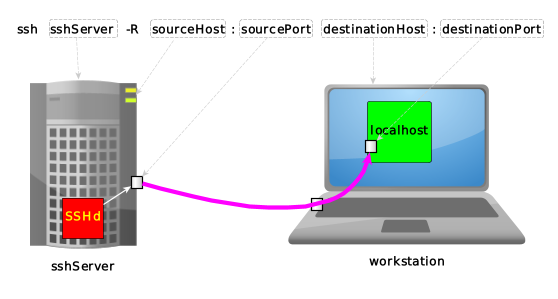
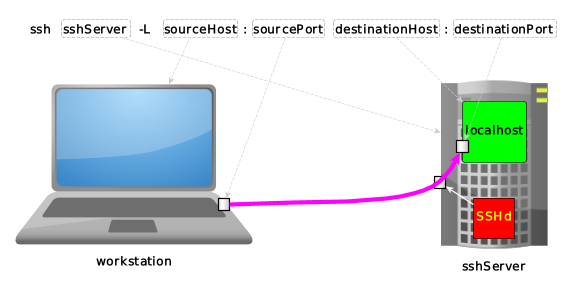
ssh sshServer -L sourceHost:sourcePort:destinationHost:destinationPort |<---+---->| |<---------+----------->| |<--------------+--------------->| | | +-------------------> tunnel exit, as seen from sshServer | +--------------------------------------------------> tunnel entrance, as seen from workstation +-------------------------------------------------------------------------> where we're connecting to via ssh
as seen from sshServer:
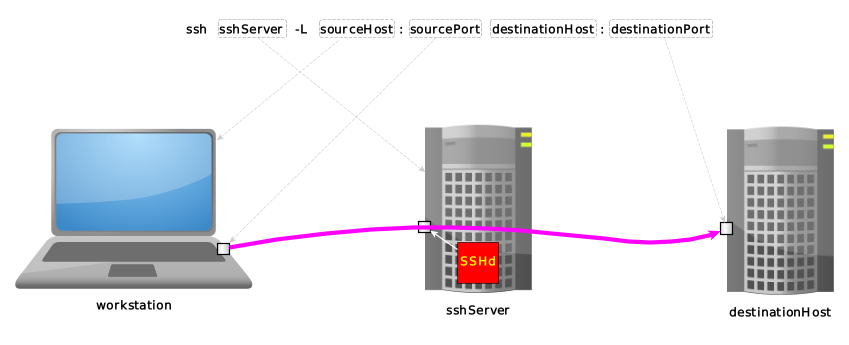
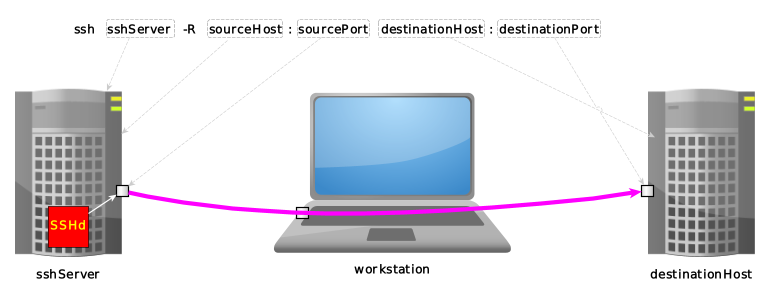
ssh sshServer -R sourceHost:sourcePort destinationHost:destinationPort |<---+---->| |<----------+---------->| |<--------------+--------------->| | | +-------------------> tunnel exit, as seen from workstation | +-------------------------------------------------> tunnel entrance, as seen from sshServer +-------------------------------------------------------------------------> where we're connecting to via ssh